Revealing the new network telecom fraud means. It was all in the middle of the night.
CCTV News:I didn’t lose my mobile phone or bank card, didn’t scan the QR code or click the SMS link, and when I woke up, the money in the bank card was gone. Some time ago, we reported the case of suspects using "sniffing" technology to steal bank cards from a distance. However, recently, Anhui police informed that several citizens in Chuzhou have encountered such a new type of online fraud.
In the early morning of July this year, Yang Xiao, a citizen of Chuzhou, Anhui Province, was awakened by the vibration of his mobile phone. In just a few minutes, he received more than a dozen SMS notifications of bank card consumption deduction. The content of the SMS showed that his bank card spent more than 50,000 yuan.

Victim Yang Xiao:The first one is 999 yuan, and then more than a dozen pens are brushed, all of which are 4999 yuan. The display time is from the early morning until after five o’clock in the morning.
At that time, Yang Xiao’s mobile phone was beside him and his bank card was not lost.
Victim Yang Xiao:The first reaction is that there is a virus in the link of the ordinary mobile phone. The mobile phone is placed next to it and the card is on the body. This kind of stolen brush has never been encountered.
After confirming that the money in the bank card was indeed brushed away, Yang Xiao rushed to the public security bureau to report the case. After reporting the case, he realized that there were already many victims like him, and the bank card was stolen late at night.
Yan Bo, Investigator of Criminal Investigation Brigade of Economic Development Branch of Chuzhou Public Security Bureau:Basically, it is from two or three o’clock at night to before six or seven o’clock in the morning. The victims are all asleep, and their mobile phones are silent and vibrating.
Chuzhou police immediately set up a task force. After several rounds of research, tracking the source of signals and the flow of funds, finally, the police locked the suspect Song, who had been transferred to Hefei, and arrested him in July. According to Song’s confession, the victim’s money was stolen by him and his associates using sniffing technology. On the day of the arrest, he was still using sniffing equipment and was ready to continue committing crimes.
Subsequently, according to Song’s confession, the police arrested all other suspects involved. At this point, a criminal gang that used "sniffing" technology to steal other people’s bank cards was uprooted.
According to the police, the most crucial link for criminal suspects to steal bank cards from a distance is that they can intercept other people’s mobile phone messages by using sniffing equipment. So how does this sniffing device work?

Suspect Song:This USB flash drive acts as a mobile interception system. Those mobile phone devices are eavesdropping devices. Because 2G is not encrypted, we are equal to being an eavesdropper. Because it is not encrypted, we can intercept it in the middle.
These seemingly crude devices in front of us are the sniffing devices used by suspects to intercept short messages from nearby residents. According to Song, as long as this device is started, the background can automatically scan the mobile phone numbers of residents within about one kilometer around. Once these mobile phone numbers are in the state of 2G network, the short messages received by residents’ mobile phones are likely to be displayed on the suspect’s computer simultaneously. Using sniffing equipment, they can intercept hundreds or even thousands of short messages a day. At the scene of the arrest, Song also gave a demonstration. About ten minutes after the sniffing device started, they received more than a dozen text messages on their computers, including mobile phone numbers, text messages and so on.
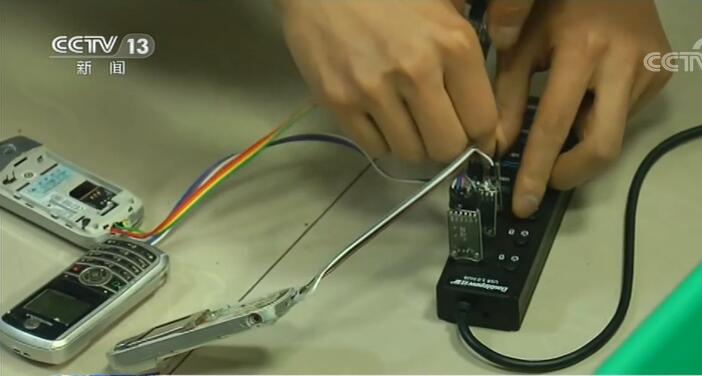

Suspect Song:Interception of mobile phone 2G SMS, or when mobile data is not turned on, has an 80% probability of interception.
Using "sniffing" equipment to intercept other people’s short messages is only the first step in committing a crime. In order to successfully steal a bank card, the suspect needs to obtain more personal information of the victim.

The reason why the suspects choose to commit crimes in the middle of the night is because most of the victims are already asleep at this time, and even if there is abnormal information on the mobile phone, it is difficult for them to find it in time. According to the police, because the suspects can intercept mobile phone messages, they use the mobile phone number+verification code to log in to some third-party software to find other personal information of the victims. However, some websites and apps still have certain technical loopholes. The suspect can easily obtain the victim’s name, ID number, bank card number, etc. by some simple hacking methods, and with the mobile phone verification code intercepted in real time, he can directly steal the money in the victim’s bank card.
It is by this means that Song and others have successfully committed more than 60 crimes in many provinces across the country in just a few months. At present, the suspect has been criminally detained by the police according to law, and the case is being further processed.
Protect personal information to prevent mobile phones from being sniffed
Using "sniffing" equipment to steal bank cards from a distance sounds terrible, but it doesn’t mean that criminals can do whatever they want. So how do we guard against it?
According to the police, in daily life, if you find that your mobile phone signal suddenly drops to 2G and you receive a short message verification code from an unknown source, it is probably scanned by criminals using sniffing equipment.
Yan Bo, Investigator of Criminal Investigation Brigade of Economic Development Branch of Chuzhou Public Security Bureau:We can temporarily turn off the mobile phone or turn on the flight mode so that our mobile phone can’t receive short messages for the time being, which makes it impossible for the sniffing device to intercept short messages in real time.
In addition, after intercepting the short message, the suspect also needs to obtain the personal information of the victim from the third-party software in order to steal the bank card. Therefore, everyone should protect their personal information, especially sensitive information such as ID number and bank card number, and don’t disclose it easily, leaving an opportunity for criminals.